Introduction to Computer Objects in AD
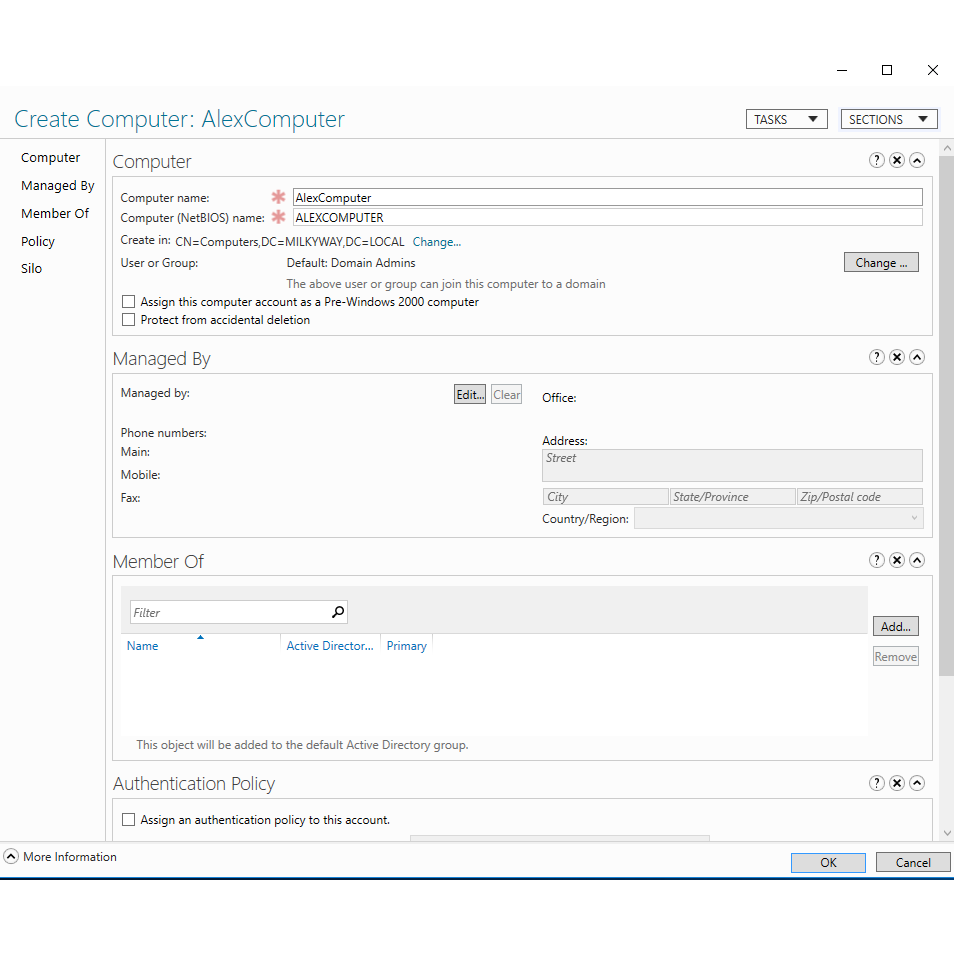
In the realm of Active Directory (AD), understanding the concept of a computer object is fundamental. A computer object is an essential element within AD as it symbolizes a computer that is part of a network. This entity serves as a representation within AD’s database, where it receives, stores, and applies policies and permissions. Computer objects are vital for network administrators to effectively manage and oversee networked computers. These objects help in defining security principles that are particular to each computer and allow for the application and enforcement of policies to ensure that machines adhere to organizational standards.
Each computer object contains crucial attributes that are specific to the computer it represents, such as its name and network configurations. These attributes enable AD to identify and differentiate each computer on the network. Moreover, the computer object facilitates the deployment of Group Policy Objects (GPOs), which are crucial in centralizing management tasks such as software installations, security updates, and configuration changes across multiple computers.
The procedure of a computer joining the domain involves creating a computer object within the AD. When this process is commenced, it is imperative for the computer’s name to be unique within the domain to prevent duplication and confusion. This incorporation into the AD domain not only integrates the computer into the network infrastructure but also enables it to be subject to AD’s authoritative domain policies.
In summarizing, computer objects in Active Directory are the backbone of network computer management, facilitating streamlined administration, security, and compliance with organizational IT policies. Understanding the intricacies of computer objects is the stepping stone to mastering Active Directory administration.
How Computers Join the AD Domain
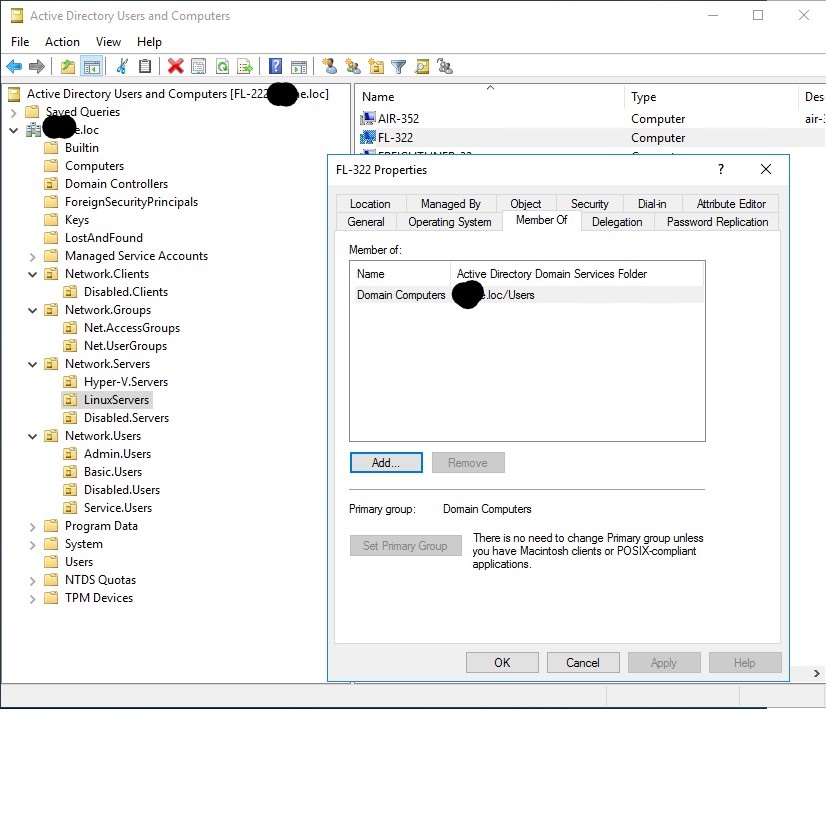
When a computer is introduced to a network running Active Directory, it must join the AD domain to be managed within that environment. This joining process is a critical step to make sure the computer complies with the necessary security and management policies set by the organization. Here’s a step-by-step walkthrough of how computers typically join the AD domain:
- Renaming the Computer (if needed) – In scenarios where a new computer is added to the network, it may need a unique name to avoid conflicts with existing computers.
- Creating a Computer Object – An account for the computer, known as a ‘computer object,’ is created in Active Directory. This may be pre-created by an admin or generated automatically upon joining.
- Joining the Domain – The computer is added to the domain using credentials with the necessary permissions, often provided by a network administrator.
- Authentication – The domain controller verifies the computer’s credentials and its unique name within the domain.
- Setting Policies – Once authenticated, the computer receives and applies Group Policy Objects (GPOs) relevant to its role and use within the organization.
By the end of this process, the computer is officially a domain member, configured to operate securely and efficiently within the AD infrastructure. This connection opens the computer to a series of advantages, such as centralized management, streamlined policy application, and enhanced security protocols. It’s important for network administrators to oversee this process to minimize issues and ensure that all systems are compliant from the get-go.
The Role of ‘Computer Object’ Names in Domain Joining
When integrating a computer into an Active Directory (AD) domain, assigning a unique ‘computer object’ name is crucial. This name must be distinct within the domain to prevent conflicts and ensure proper management. Here are key points about the role of computer object names in the domain joining process:
- Uniqueness is Mandatory – Computer object names in AD must be unique to avoid duplication. If a duplicate name exists, the system will reject the new computer’s addition to the domain.
- Name Reflects Identity – The computer object name serves as the computer’s identity within the AD. It helps in recognizing the machine across the network and managing its configurations and policies.
- Automatic or Pre-set – When joining a domain, if the computer’s object name isn’t pre-existing, AD can automatically create one based on set naming conventions.
- Error Handling – If an attempt is made to add a computer with a name that already exists, an error is generated. This prevents unauthorized duplications and preserves the integrity of the domain structure.
- Permissions Are Key – Only users with adequate permissions, like network administrators, can add new computers to the domain. This includes naming the computer objects and resolving any naming conflicts that may arise.
In essence, the designation of computer object names is not just a mere formality but a pivotal step in guaranteeing smooth, structured domain operations. It assists network administrators in maintaining a well-organized and secure AD environment.
Managing Computer Accounts: Creation and Duplication
When administering an Active Directory (AD) environment, managing computer accounts effectively is a critical task. Here are the essentials you need to know about creating and avoiding duplication of computer accounts:
- Pre-creation Vs. Automatic Creation: Network administrators can pre-create computer objects in AD before adding computers to the domain. Alternatively, AD can generate a computer object automatically during the domain joining process.
- Avoiding Name Conflicts: Ensuring each computer object has a unique name within the AD domain is fundamental. AD does not permit two computers with the same name to coexist within a domain to maintain order and prevent conflicts.
- Error Messages for Duplicates: If a computer is added with a name that already exists, AD generates an error. This stops the duplication process and alerts the administrator to the issue.
- Renaming for Resolution: In cases where a conflict arises, renaming the new computer is a necessity. This action establishes a unique identity and allows for successful domain joining.
- Permission Control: Only users with sufficient privileges can create computer objects and join computers to the domain. These permissions help prevent unauthorized changes and maintain security.
By paying close attention to computer object creation and handling potential duplications proactively, network administrators can ensure a robust and streamlined AD infrastructure.
Understanding GPOs: Computer vs. User Configuration
To fully grasp how Active Directory (AD) governs network computers, it’s essential to understand Group Policy Objects (GPOs). GPOs are central to AD’s ability to manage user and computer settings across an organization. They contain rules that determine how computers and users should behave within the domain. Here’s a breakdown of the differences between computer and user configurations in GPOs:
Computer Configuration
This part of a GPO pertains to settings that apply to the computer itself, regardless of which user logs in. Such configurations take effect at system startup or reboot and reapply every 90 to 120 minutes by default. Common policies include security settings, software installations, and startup scripts.
User Configuration
In contrast, user configuration settings are specific to user accounts. They are applied when a user logs onto the computer and are refreshed similarly every 90 to 120 minutes. These can include desktop settings, file redirection, and certain security permissions tailored to the user’s role.
Both configurations are distinct and separately applied. A GPO targeted at a user will not affect the computer configuration and vice versa. To make sure settings are effectively applied, it’s best practice to create separate GPOs for users and computers. This method avoids confusion and ensures that policies are applied correctly to the intended targets.
It’s also important to resolve conflicts that may arise when computer and user configurations overlap. For example, if one policy locks down a setting but a user-configured GPO attempts to change it, which one takes precedence? AD resolves this by applying computer configurations before user settings, ensuring that system-level policies remain secure.
By keeping user and computer configurations clear and separate, and understanding the application process, network administrators can maintain order and enforce policies effectively within their organizational structure. This understanding is paramount for robust network management and security.
The Machine Account Quota – What It Is and Its Implications
The Machine Account Quota is a crucial aspect of network management in Active Directory. It sets limits on the number of computer objects a user can create. Here are the key points to understand about this quota and what it means for your network:
- Definition and Default Limit: The quota refers to the maximum number of computer objects a non-administrative user can add to the domain. By default, this limit is set to 10 computer objects per user.
- Ensuring Control: The Machine Account Quota is there to prevent unauthorized proliferation of computer objects. It helps maintain control over who can add computers to the network.
- Adjusting the Quota: Administrators have the power to adjust this quota. They can increase or decrease the number per user based on the organization’s needs.
- Implications of Zero Quota: If the quota is set to zero, only users with administrative privileges can add new computer objects. This is often used to tighten security and ensure proper oversight.
- Quota Exceeded: When a user tries to add a computer and the quota is exceeded, AD will deny the request. This prevents users from adding more computers than permitted.
- Impact on Small vs. Large Organizations: In small organizations, the default limit might suffice. However, in larger setups with many users adding computers, adjustments may be necessary.
Understanding the Machine Account Quota is essential for admins. It helps prevent unauthorized additions of computer objects and ensures a manageable number of machines within the domain. Managing this quota effectively can significantly impact network security and orderliness.
Deep Dive into AD ‘Containers’ and Organizational Units
Active Directory uses two primary types of containers: ‘Containers’ and Organizational Units (OUs). Let’s delve into what they are and how they differ.
Active Directory ‘Containers’ are default locations provided by AD to store objects like users, computers, and groups. For example, the ‘Computers’ container is a default location for computer objects when they’re first added to the domain.
Organizational Units (OUs), on the other hand, are custom containers created by network administrators. They group together objects for easier management and application of GPOs. OUs offer a level of flexibility that default ‘Containers’ do not.
Here are key insights into these pivotal elements of AD infrastructure:
- Flexibility of OUs: Administrators can create, delete, and move OUs to reflect the organizational structure. This feature offers tailored administration.
- GPO Linkage: OUs can have unique GPOs linked directly to them, governing the behavior of objects within. This allows for granular policy control.
- Delegation of Control: Admins can delegate control over OUs to other users. This spreads out management responsibilities without handing over full domain control.
- Visibility and Structure: OUs make the AD more transparent. They help in visualizing the structure of the organization within the directory service’s hierarchy.
- ‘Containers’ vs OUs: Unlike OUs, ‘Containers’ cannot have GPOs linked directly to them. They are less flexible but serve essential roles within the AD domain.
Understanding the distinction between these two types of containers is crucial for effective AD administration. It allows for strategic organization and management of resources within the business network. By leveraging OUs, admins can enforce specific policies and delegate roles, ensuring that network resources align with the company’s operational and security standards.
The Significance of Loopback in GPO Applications
In Active Directory (AD), managing policy applications effectively is critical. This is where the Loopback processing mode comes into play, a feature that significantly influences Group Policy Object (GPO) applications. Loopback processing alters the standard policy application process, ensuring that certain user policies apply based on the computer they log onto, rather than simply following the user account.
Loopback processing is beneficial in environments like public kiosks, classrooms, or labs, where computers are accessed by multiple users, but a consistent setup is required regardless of who logs in. Here are the key points:
- Loopback Processing Modes: There are two modes – Replace and Merge. ‘Replace’ means the user policies defined by the computer’s GPOs completely override user-specific policies. ‘Merge’ combines both sets of policies, with computer GPOs taking precedence.
- User-Specific Policies Override: In a loopback setting, policies applied directly to the computer can overwrite user-specific policies. This ensures a uniform configuration for everyone using the computer.
- Complexity and Consideration: Loopback can add complexity to policy management as administrators need to carefully consider the interplay between user and computer policies to avoid conflicts and ensure the policies execute as intended.
- Unexpected Behavior Handling: Proper planning and testing are necessary to predict how policies will apply in a loopback scenario to avoid unexpected results, especially when the Merge mode is used.
- Applicability: Whether to use loopback processing should be based on network simplicity and specific use cases. For simple networks, standard GPO application might suffice. However, for specialized setups, loopback can be highly effective.
In conclusion, loopback processing holds significant importance in tailored GPO applications, providing the flexibility to ensure a consistent and secure user experience across shared computers. Understanding and managing loopback mode is part of an administrator’s toolkit within a well-organized AD infrastructure.
Distinguished Names in Active Directory: Understanding OU and DC
Navigating the structure of Active Directory (AD) requires an understanding of Distinguished Names (DN). Distinguished Names are the unique paths that precisely identify each object within the AD hierarchy. Let’s break down the components of a DN, specifically Organizational Units (OU) and Domain Components (DC), and their implications in AD management.
Organizational Units (OU)
OUs provide a way to organize and manage groups of AD objects. They allow administrators to apply specific GPOs and delegate administrative rights. An OU is the container where related objects, like user accounts and computer objects, reside.
Domain Components (DC)
DCs form the part of a DN that references the AD domain name. They reflect the domain’s structure in LDAP format, converting domain segments into a path-like string.
When a computer object is created in AD, the DN includes both OUs and DCs to determine its location within the domain. For instance, if a computer object is part of the ‘ApplicationServers’ OU in the domain ‘example.com’, its DN might look like this: OU=ApplicationServers,DC=example,DC=com.
Creating Computer Objects Using DN: To create a new AD computer object, you might use tools like PowerShell. When specifying the -Path parameter in the New-ADComputer cmdlet, you are defining the DN for the new computer object.
Uniqueness and Implications: Every object in AD must have a unique DN to avoid conflicts. If you try to create a computer with a DN that already exists, AD will reject the attempt and produce an error, maintaining the integrity and uniqueness within the domain.
Finding the DN: You can find the DN of an OU or computer object through the AD Users and Computers console. This DN is then used to structure the AD and align it with the company’s organizational setup.
Understanding OUs and DCs within DNs is essential for effective AD management. It ensures that objects are correctly placed and policies are appropriately applied in the domain, paving the way for an organized and secure network infrastructure.